GitHub Action Integration¶

In this guide we'll show you how to set up a GitHub Actions Workflow so Mayhem can automatically test your Code or API on every push.
You will need the following to run Mayhem in your GitHub Action workflows:
Note: You can use the same token to test your Code or API.
- Create a Mayhem API token.
- Add the newly created token to your GitHub secrets using a variable named
MAYHEM_TOKEN.
Workflow Configuration for Testing your Code¶
The Mayhem GitHub Action tests every change to your code by kicking off a CI workflow (below we show example usage through GHCR and Docker Hub), building and pushing a Docker image for your target application, automatically testing it, with a final security testing or SARIF report generated at the end of the workflow.
Getting Started¶
Integrating the GitHub Action into your GitHub repository is easy! If you're using either the GitHub Container Registry (GHCR) or Docker Hub as your image registry, follow the corresponding steps:
mCode Action using GHCR:
-
Add the following to your GitHub Secrets for your GitHub repository.
MAYHEM_TOKEN: Your Mayhem token.MAYHEM_URL: The URL of the Mayhem instance, such ashttps://app.mayhem.security.-
Ensure your repository's package visibility settings are set to
Publicto give Mayhem permissions to ingest your Docker image from the GitHub Container Registry.Click on your package in the right-hand pane of your GitHub repository and go to Package Settings. Then, scroll down to Package Visibility and set the package to
Public.
-
Create a
Dockerfileat the root of the repository for your containerized application. - Create a
Mayhemfileat the root of the repository for configuring the Mayhem run on your containerized target application invoked by the mCode GitHub Action. - Create a
mayhem.ymlworkflow at.github/workflows/mayhem.ymlthat builds and pushes a Docker image and uses the mCode GitHub Action to fuzz your containerized application in a CI pipeline.
mCode Action using Docker Hub:
-
Add the following to your GitHub Secrets for your GitHub repository.
DOCKER_USERNAME: Your Docker Hub username (this is case-sensitive).-
DOCKER_PASSWORD: Your Docker Hub password.If you have 2FA enabled, you must set up an access token for your Docker Hub account. Specify the access token as your
DOCKER_PASSWORDin your GitHub Secrets. -
MAYHEM_TOKEN: Your Mayhem token. MAYHEM_URL: The URL of the Mayhem instance, such ashttps://app.mayhem.security.
-
Create an associated Docker Hub repository for your GitHub repository.
For example, the GitHub repository
mayhemuser/lighttpd-demowill require an associated Docker Hub repository namedmayhemuser/lighttpd-demo, as the Docker image built and pushed to Docker Hub during the pipeline will be tagged according to the GitHub repository. -
Create a
Dockerfileat the root of the repository for your containerized application. - Create a
Mayhemfileat the root of the repository for configuring the Mayhem run on your containerized target application invoked by the mCode GitHub Action. - Create a
mayhem.ymlworkflow at.github/workflows/mayhem.ymlthat builds and pushes a Docker image and uses the mCode GitHub Action to fuzz your containerized application in a CI pipeline.
Configuring the mCode Action¶
To use the mCode Action, you'll need to add a mayhem.yml file to the fully qualified path .github/workflows/mayhem.yml in your GitHub repository. This is the configuration file for the mCode GitHub action workflow.
Your mayhem.yml should look similar to the following:
Note
The following mayhem.yml is fully-qualified and displays both required and optional input parameters (required fields are highlighted). To understand more about the available input parameters to mayhem.yml, check out mCode Action Usage.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 | |
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 | |
We can see from the mayhem.yml that the following GitHub Action plugins are executed in sequence for the pipeline runner node:
Info
actions/checkout: Your code is checked out from your GitHub repository.docker/login-action: Logs into the GitHub Container Registry using your GitHub Secrets credentials.docker/metadata-action: Used to extract metadata from Git reference and GitHub events for tagging and labeling Docker images.docker/build-push-action: Your code is built and pushed to the GitHub Container Registry as a Docker image.ForAllSecure/mcode-action: Mayhem ingests your GitHub Container Registry image and begins fuzzing your containerized target applications.github/codeql-action/upload-sarif: A SARIF report is generated from fuzz testing results and uploaded to GitHub for your repository.
Info
actions/checkout: Your code is checked out from your GitHub repository.docker/setup-buildx-action: Docker is installed.docker/metadata-action: Sets up the tag for the soon-to-be uploaded Docker Hub image.Log in to Docker Hub: Logs into Docker Hub using your GitHub Secrets credentials.Build and Push: Your code is built and pushed to Docker Hub as a Docker image.Mayhem Scan: Mayhem ingests your public Docker Hub image and begins fuzzing your containerized target applications.Upload SARIF file(s): A SARIF report is generated from fuzz testing results and uploaded to GitHub for your repository.
🤔 Still have questions? Take a look at the mcode-actions-examples repository to view working examples integrated with the mCode GitHub Action that you can use as a template. Feel free to fork the repository as needed!
Analyzing SARIF Reports¶
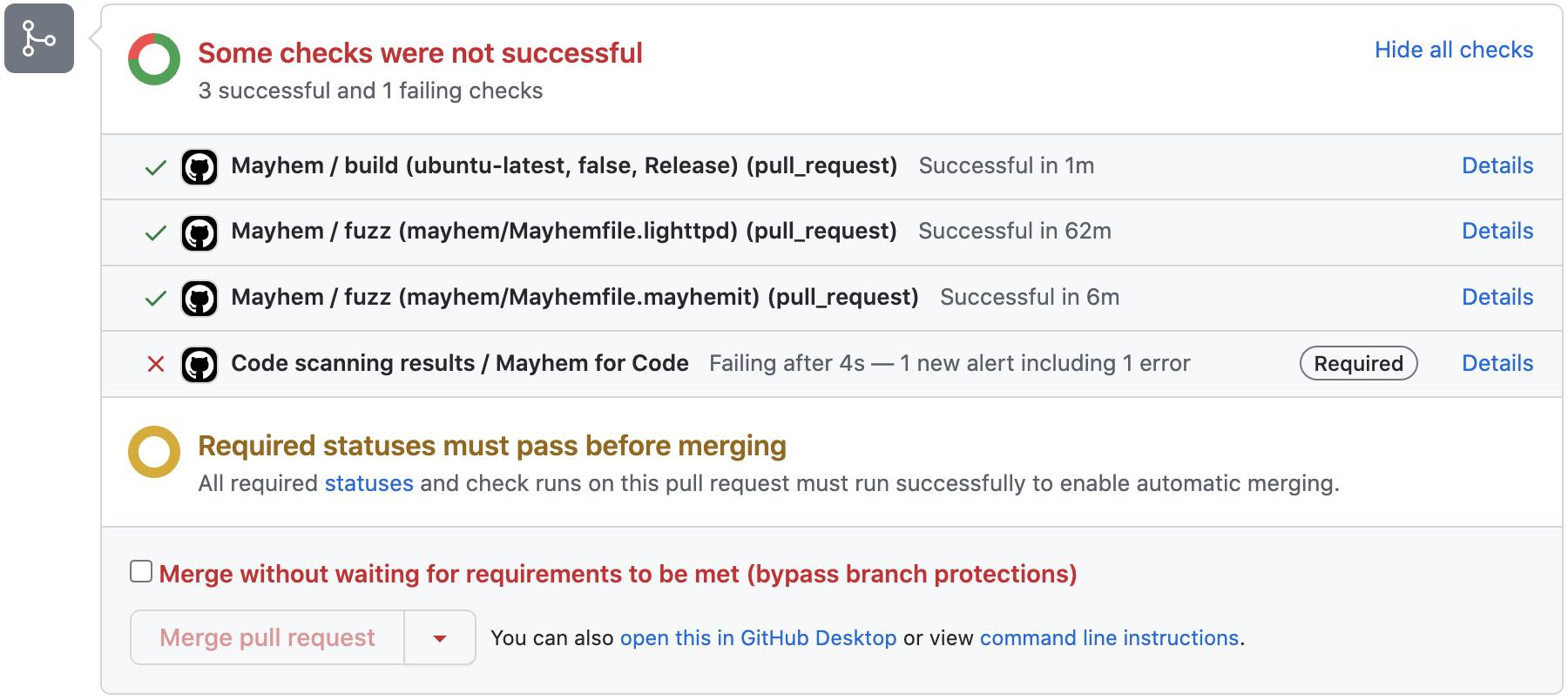
After Mayhem has fuzzed your containerized target application via the uploaded Docker image, issues that are found by Mayhem will be generated as a SARIF report and uploaded to GitHub, allowing you to view these results either in the pull request itself or in the Security tab of your repository.
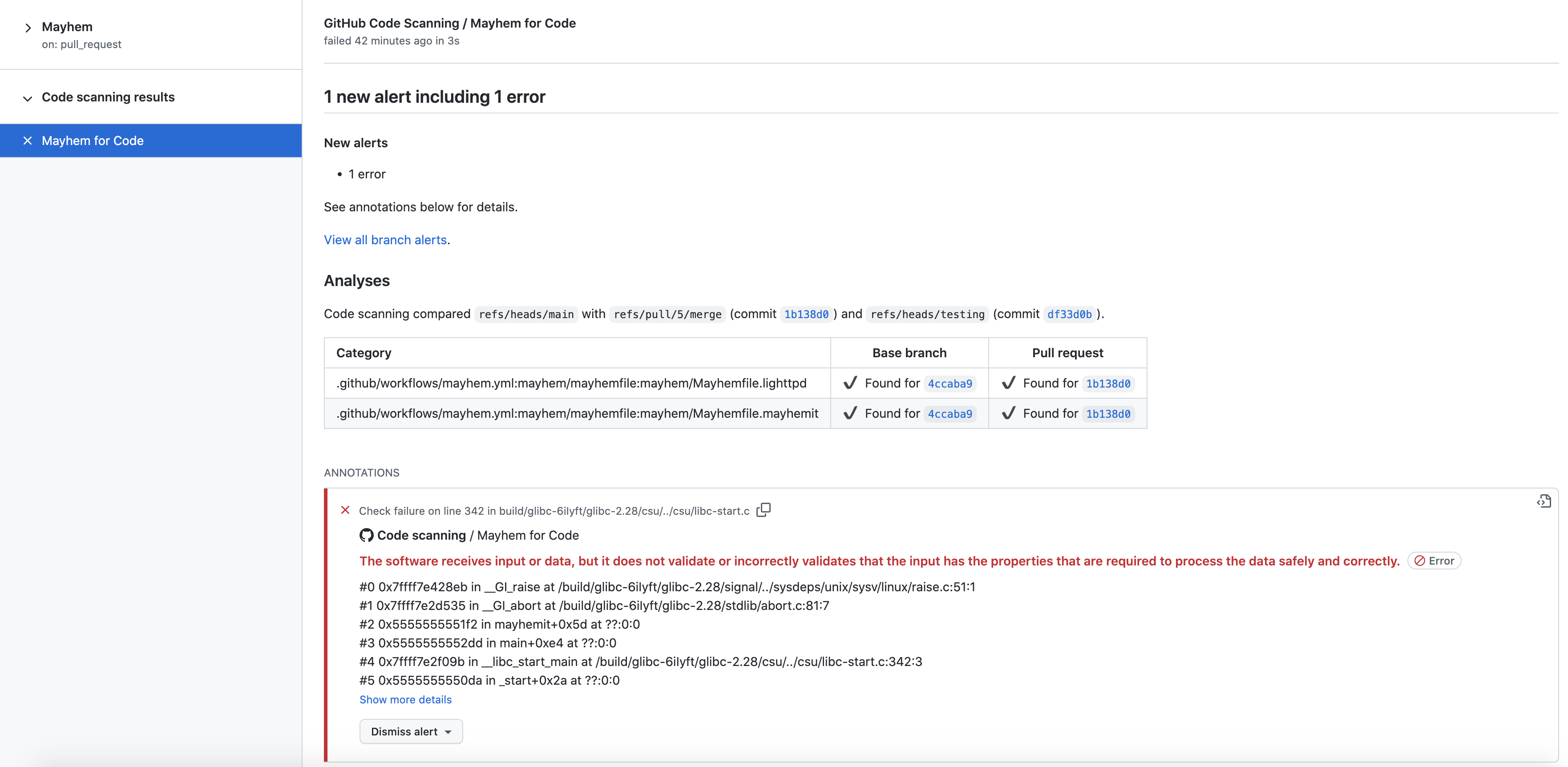
For example, if we click Details for the required Mayhem code scanning check in the pull request, we can view additional info about what Mayhem has found.
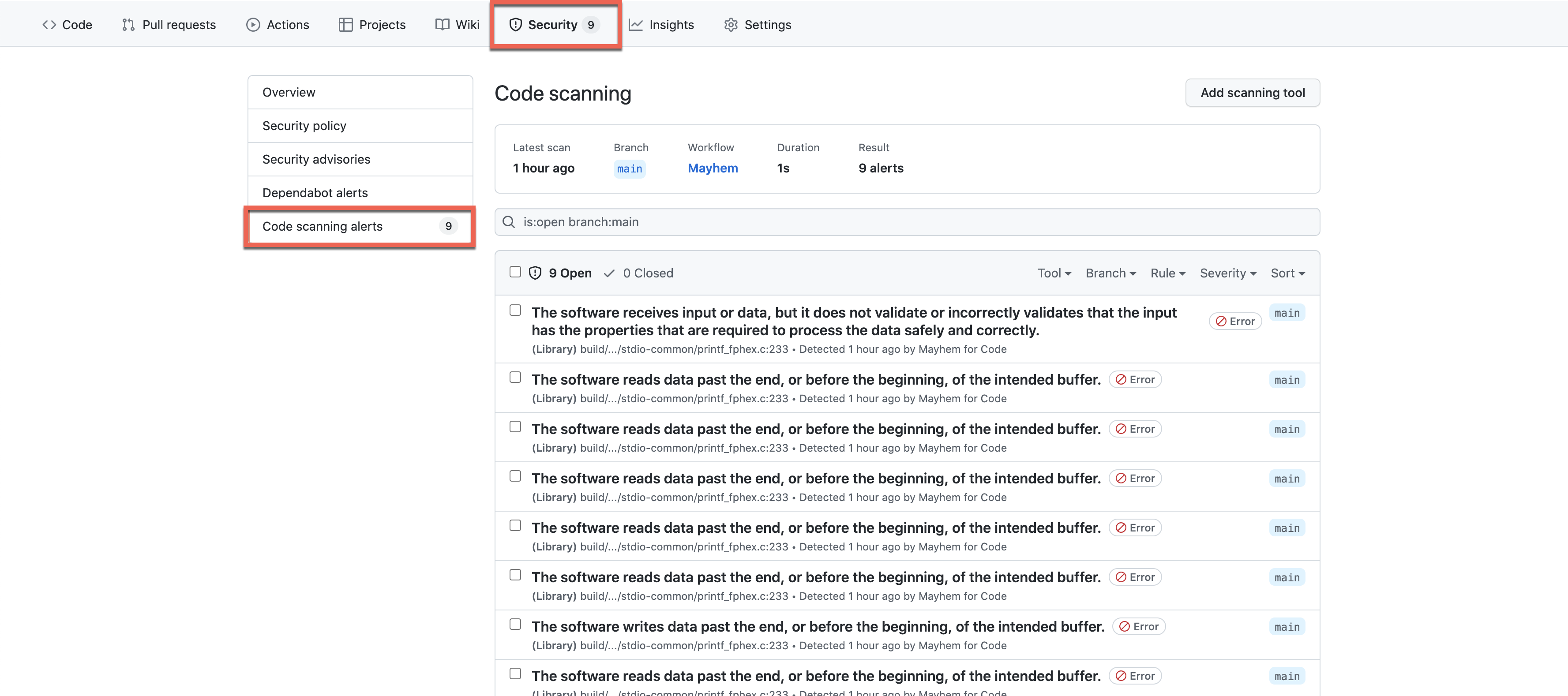
Otherwise, users can view security issues under Security > Code scanning alerts for their respective GitHub repositories.
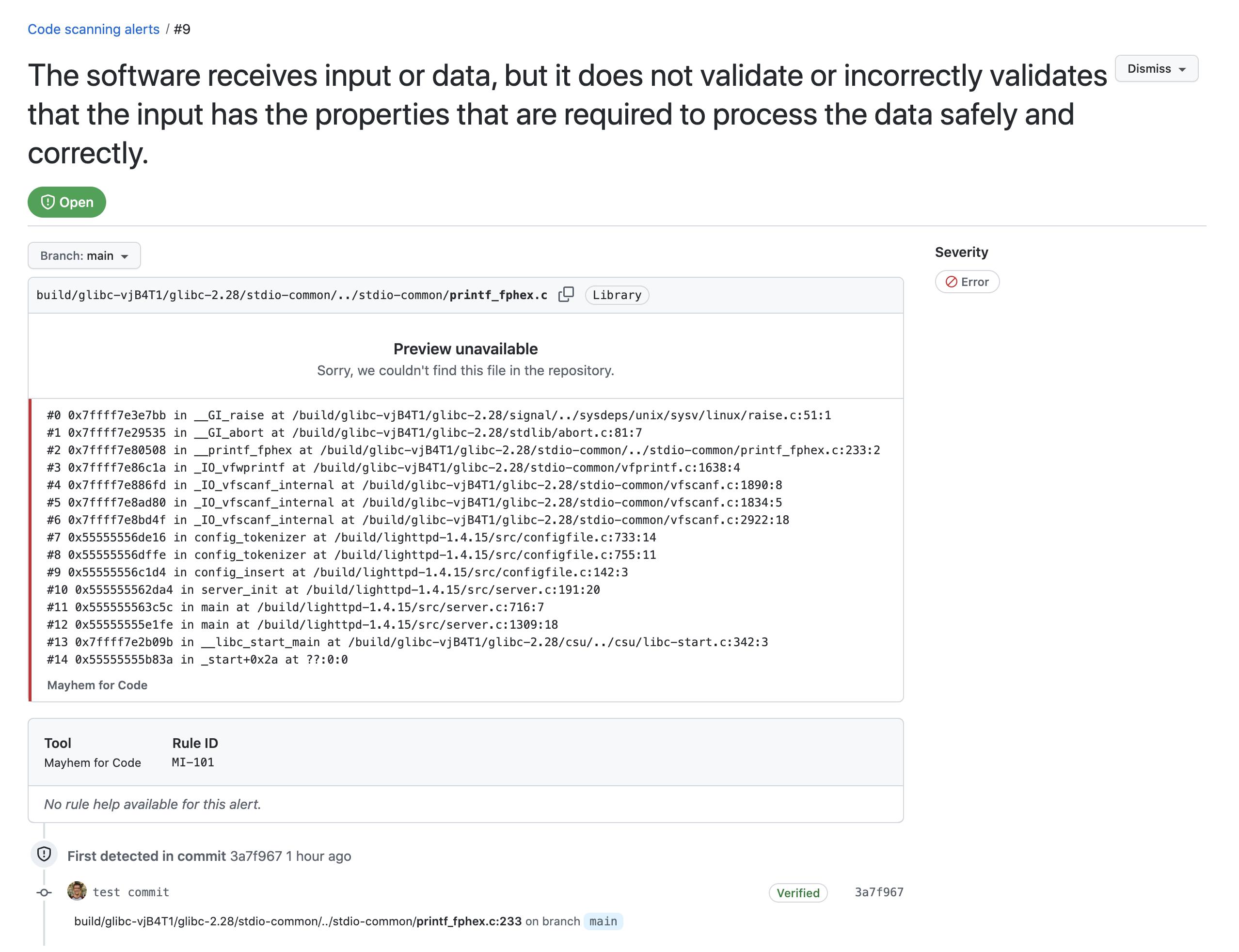
And if we click on one of the following code scanning alerts, we can view the specific commits, timelines, and branches of when these security issues were introduced or fixed.
Generating SARIF Reports via Mayhem CLI¶
Alternatively, users have the option to generate SARIF reports via the Mayhem CLI. Users can invoke a mayhem run and mayhem wait --sarif <SARIF> combination to do this.
Info
Check out the Mayhem CLI Commands page for more information on the mayhem run and mayhem wait commands.
Once the SARIF report has been generated, users can upload a SARIF file to GitHub to then view the results in the Security tab of their GitHub repositories.
Workflow Configuration for Testing your API¶
With our GitHub Action, you'll get Mayhem testing every API change in no time.
At the base directory of your code repository, add a .github/workflows/mapi.yml file to configure GitHub Actions to run Mayhem. Your file should look like this:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 | |
This configuration tells GitHub Actions to run a workflow which checks out your code, starts your API, and then runs Mayhem against your API. We pass the Mayhem token from the GitHub secret, MAYHEM_TOKEN.
Here's a fully working example repository showing you an ideal integration that you can use as a template. For more details on the Mayhem Action, visit the MAPI Action in the GitHub Actions marketplace.
SARIF Reports and GitHub Code Scanning¶
If you are testing a public repository, or a private repository on a GitHub Enterprise plan, we recommend generating a SARIF report. Mayhem can generate SARIF files with the --sarif argument to mapi run. SARIF files are a great way to upload issues to GitHub, if you happen to use GitHub.
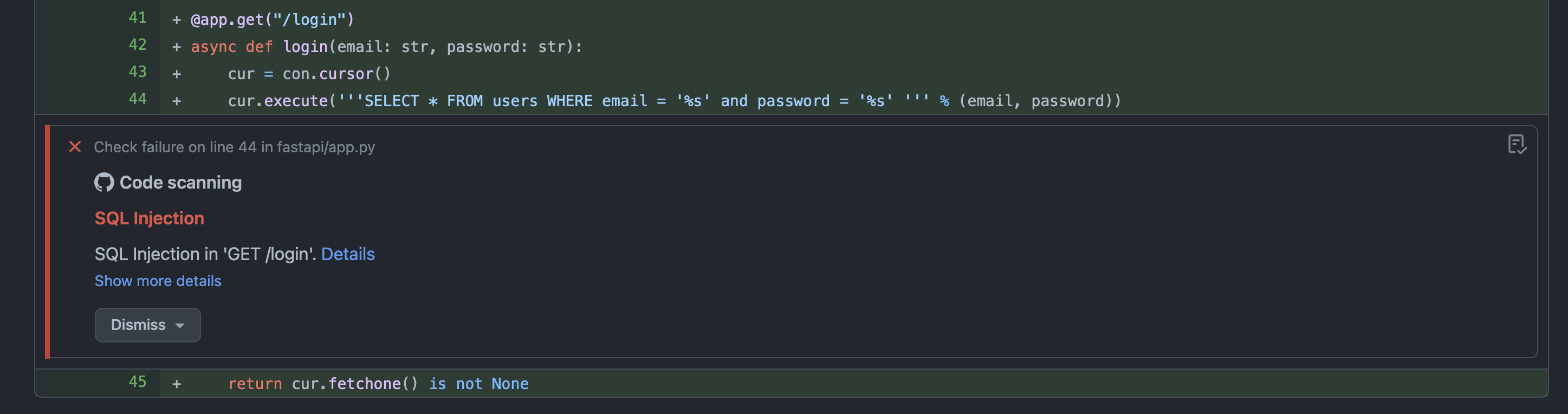
Mayhem Issues in GitHub
SARIF files can also be loaded in VSCode using a SARIF extension from Microsoft:
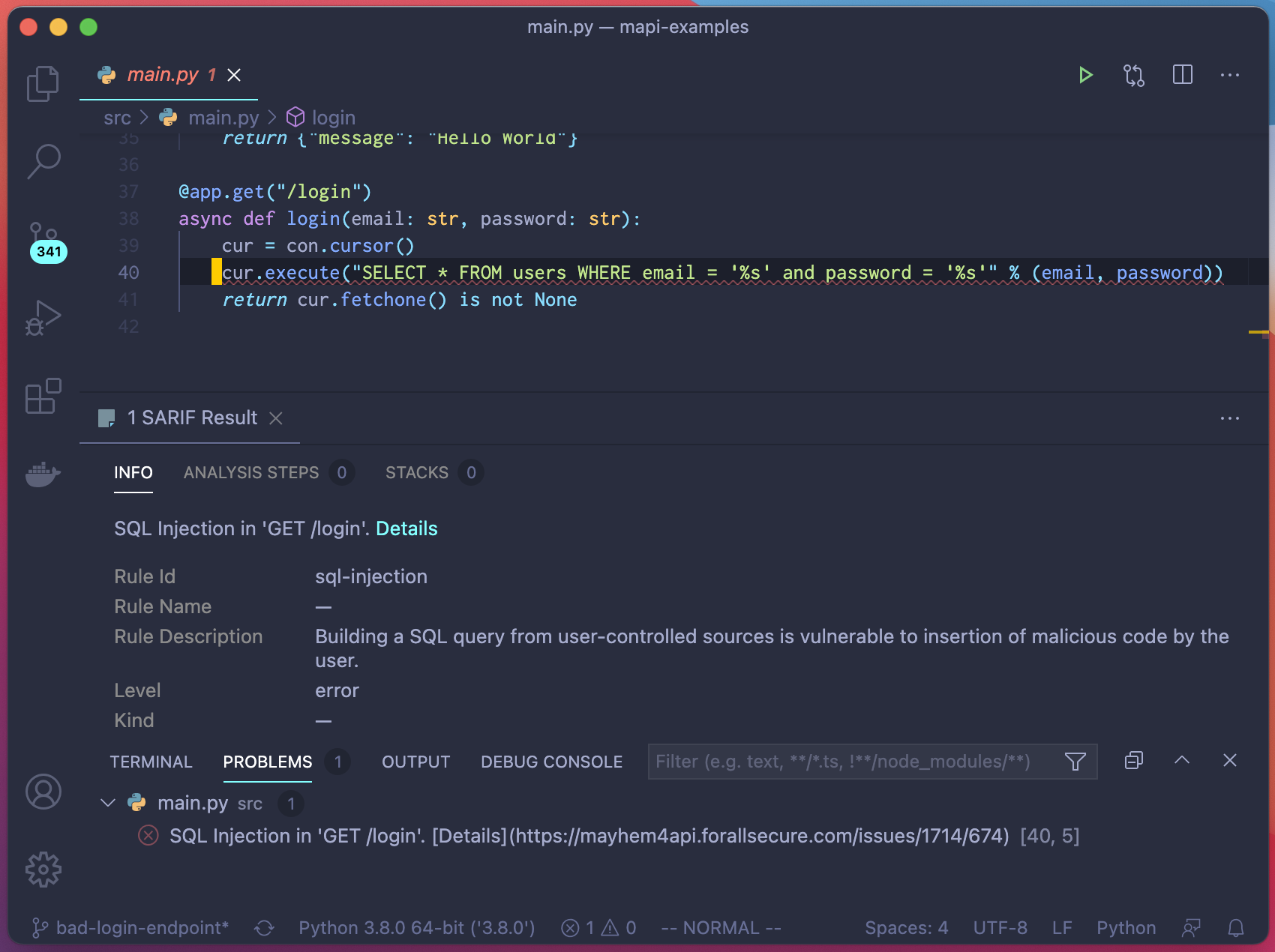
Mayhem Issues in VSCode
Info
To give accurate file and line information for each issue, Mayhem requires your API to include stacktraces in the body of "500 Internal Server Error" responses. Only do that in dev & testing -- never in production!
Uploading SARIF reports to GitHub allows you to see any issue found by Mayhem in the "Security" tab of your repository. In addition, if your API is sending back stacktraces as part of the error response body, Mayhem will show you exactly where in your code the issue happened, right in your PR diffs.
Using GitHub action¶
To do so with our GitHub Action, after starting your API in the workflow, run the Mayhem action followed by github/codeql-action/upload-sarif@v1 to upload the report.
Note
continue-on-error needs to be set to true in the Mayhem action in order to run the next step, even if Mayhem finds issues.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
Using our CLI¶
To upload our results to GitHub code scanning from anywhere, locally or from a CI, you can use our CLI. You'll need to pass a GitHub token with the security_event scope so that Mayhem can upload findings. See GitHub documentation on creating access tokens for more information. Once you have your token, simply run:
mapi run "<target>" "<duration>" "<spec>" --sarif "mapi.sarif" --github-token "<github-token>"
Mayhem will attempt to infer the git information from the environment set by the CI, and the git repository on the filesystem. If those are not available, Mayhem will ask you to pass the missing information so that it can upload the findings to the right place.
In addition, Mayhem also supports GitHub Enterprise on premise! Just pass --github-api-url <your-github-api-url> to mapi run so that Mayhem knows where to upload the results. Your GitHub instance needs to be accessible from the host running our CLI, but it does not need to be accessible by our cloud infrastructure.
Helpful Tips¶
The below sections are some helpful tips that we recommend (but are not required) and are intended to maximize your experience with the mCode GitHub Action.
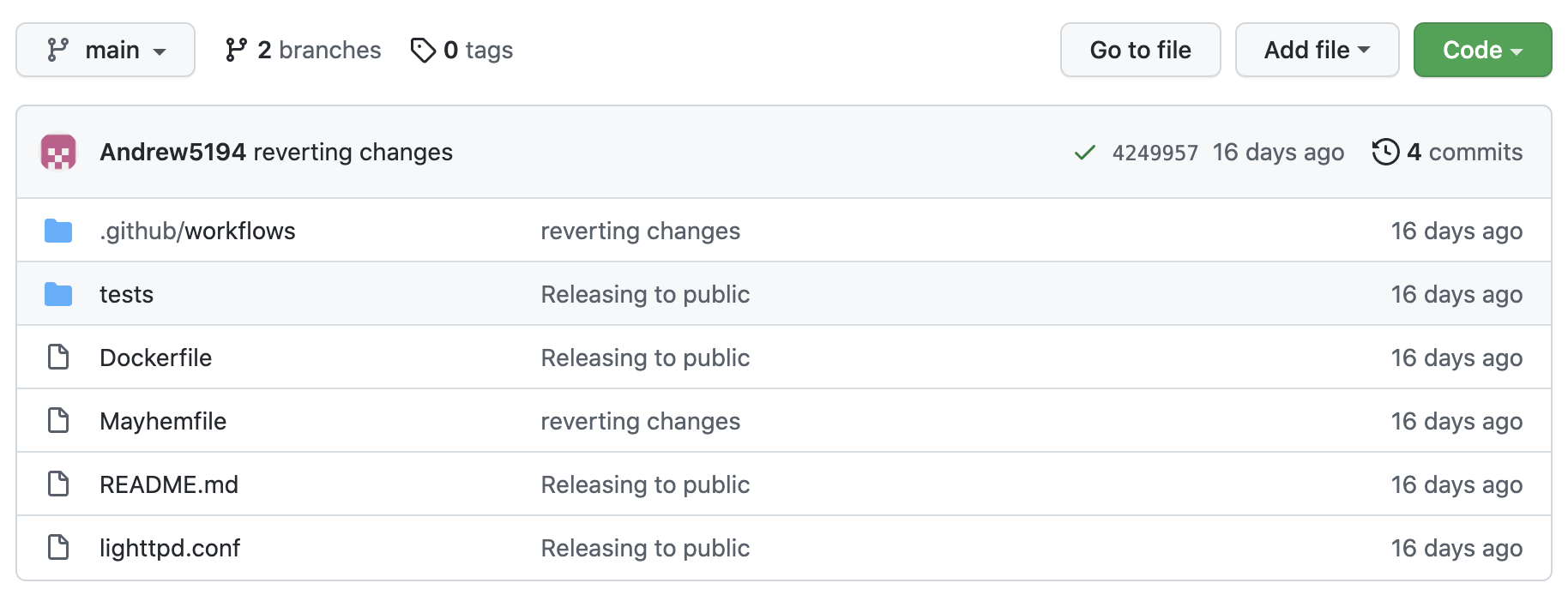
Organizing Mayhem Assets in GitHub¶
When using the mCode GitHub Action, it's important to know how to structure your files in your GitHub repository so that the mCode GitHub Action can properly build, push, and test your containerized target application.
The following files are required in order to use the mCode GitHub Action:
mayhem.yml: The configuration file for the mCode GitHub Action workflow. This must be located at.github/workflows/mayhem.yml.Dockerfile: The build file for creating a Docker image for the containerized target application.Mayhemfile: The configuration file for executing a Mayhem run for the specified containerized target.
However, overall we recommended the following file hierarchy for storing Mayhem assets in GitHub:
├── GitHub Repository
└── .github
└── workflows
└── mayhem.yml
└── README.md
└── mayhem
└── testsuite <-- The compilation of test cases for the target. Can be used to seed a Mayhem run.
└── Mayhemfile.mayhemit-c
└── Mayhemfile.lighttpd
└── Dockerfile
└── Mayhemit-c
└── lighttpd
Note
We recommend structuring your repo file organization in such a manner, but of course, this will depend on your personal preference.
As an example, see the file structure of the mcode-action-examples repository:
Adding Mayhem Project Badges in GitHub¶
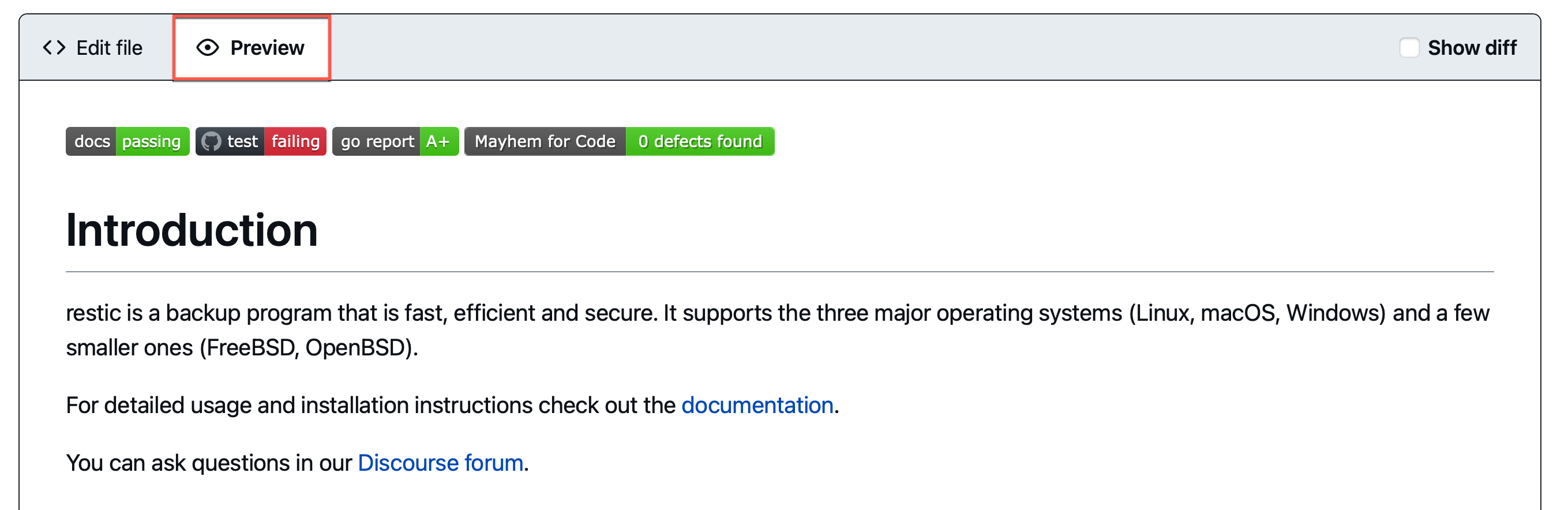
Want to display a Mayhem project badge in your GitHub repository to quickly identify if Mayhem has found defects? Now you can do this in only a few easy steps! 🎉
To add a project badge to a GitHub repo, perform the following steps:
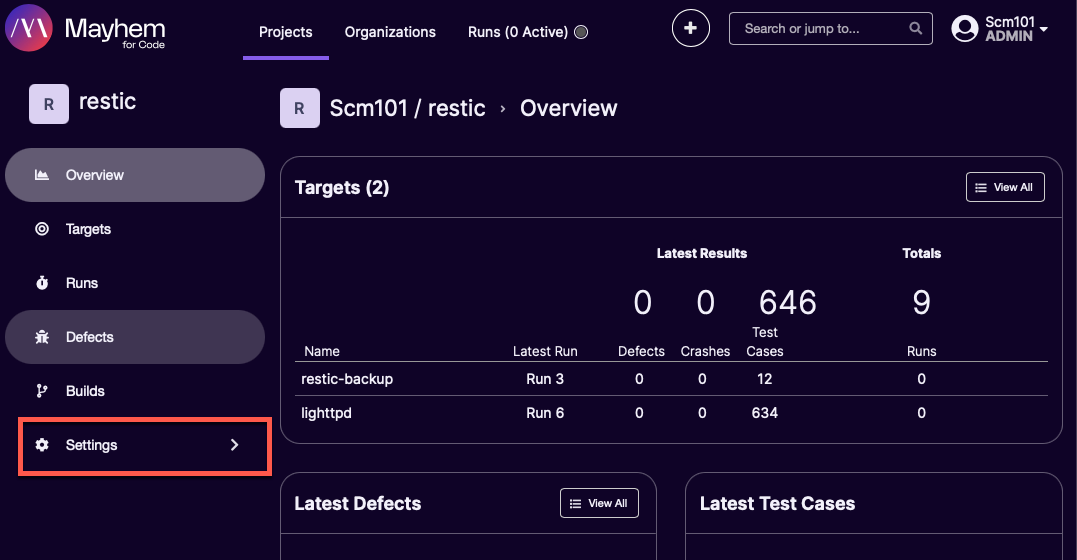
-
Navigate to the Mayhem UI and go to Project at the top of the home page. Select an existing project and then go to Settings > General in the left nav-pane for the project.
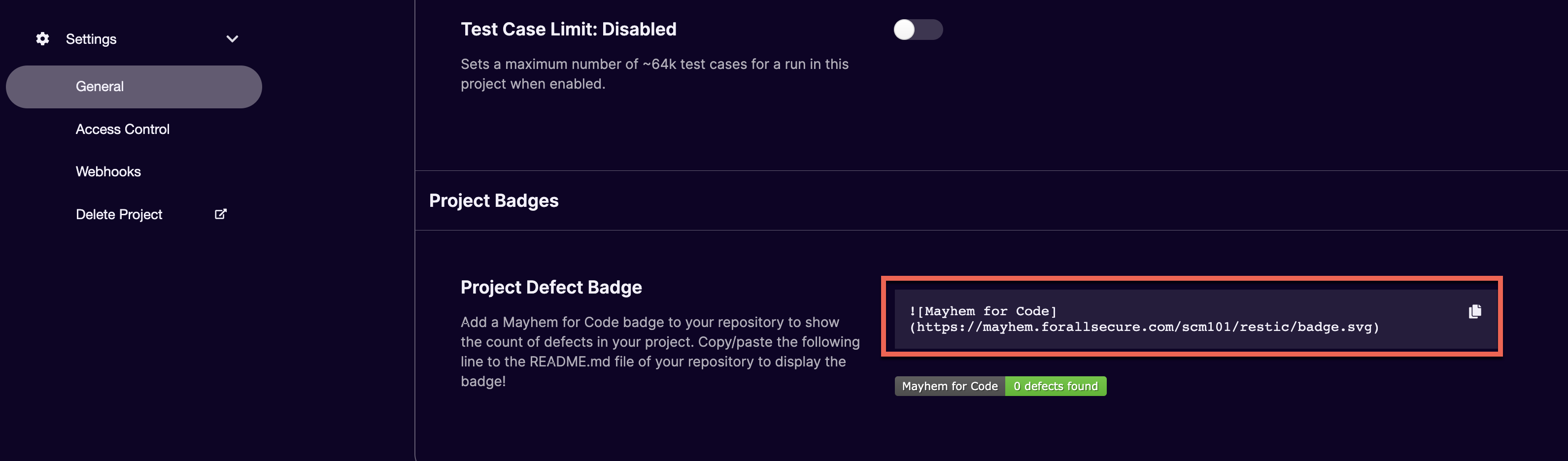
-
Scroll down to the Project Badges section: a markdown link for a dynamically generated SVG badge and description about what the badge is should be available.
-
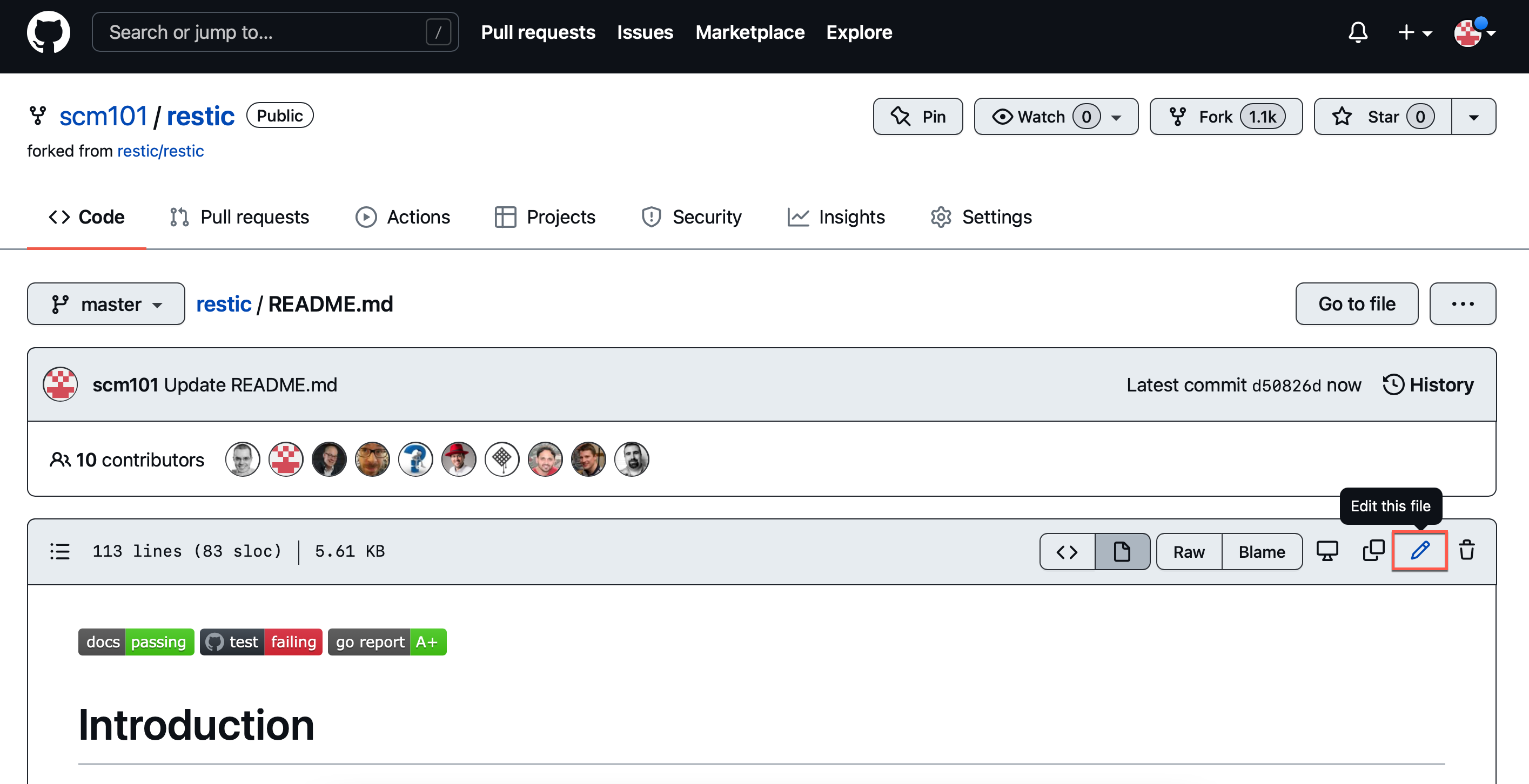
Navigate to the GitHub repo where you want to add a project badge and edit the
README.mdfile. -
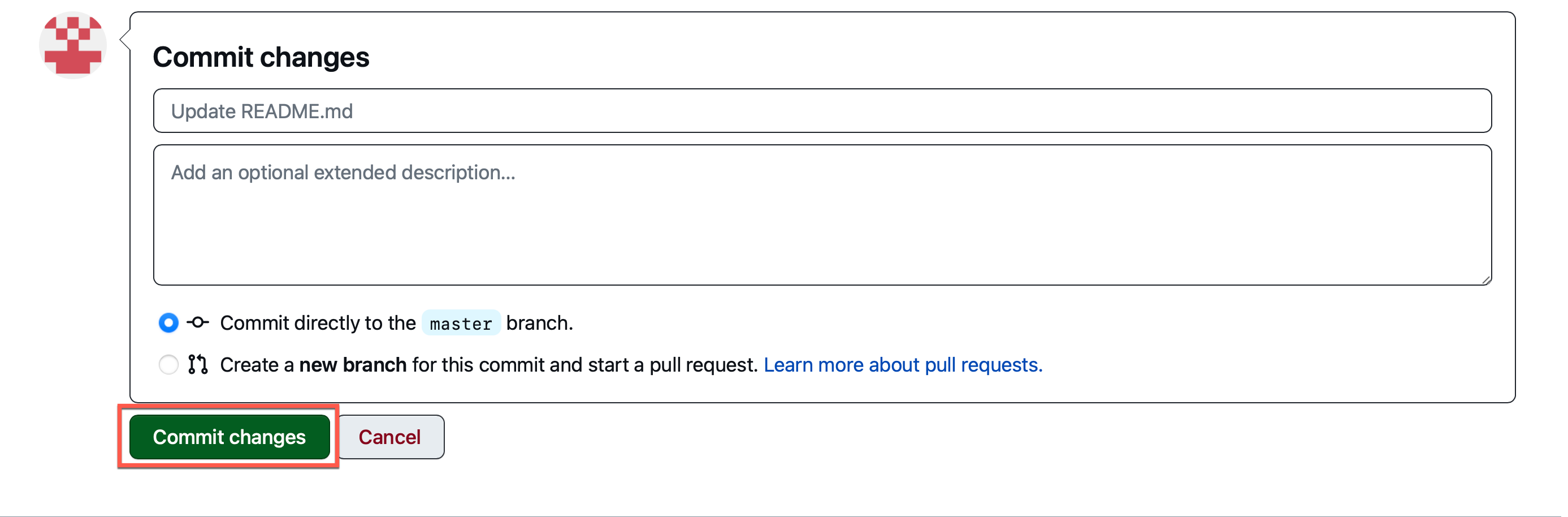
Paste the badge link from the previous step and confirm the badge is properly rendered using the Preview button.
-
Once you confirm the badge is properly rendered, commit the changes to the
main/masterbranch. -
And you’re done! You just added a Mayhem project badge to your GitHub repo!
Now you can display Mayhem project badges for your GitHub repositories! Use these project badges to quickly show information about your Mayhem project and its associated runs.
Protecting Branches and Setting Required Checks¶
Optionally, users can set required pull requests, approvals, and Mayhem required checks to better secure their code and prevent instances in which code changes with potential vulnerabilities are merged into the main or master branch of their GitHub repositories.
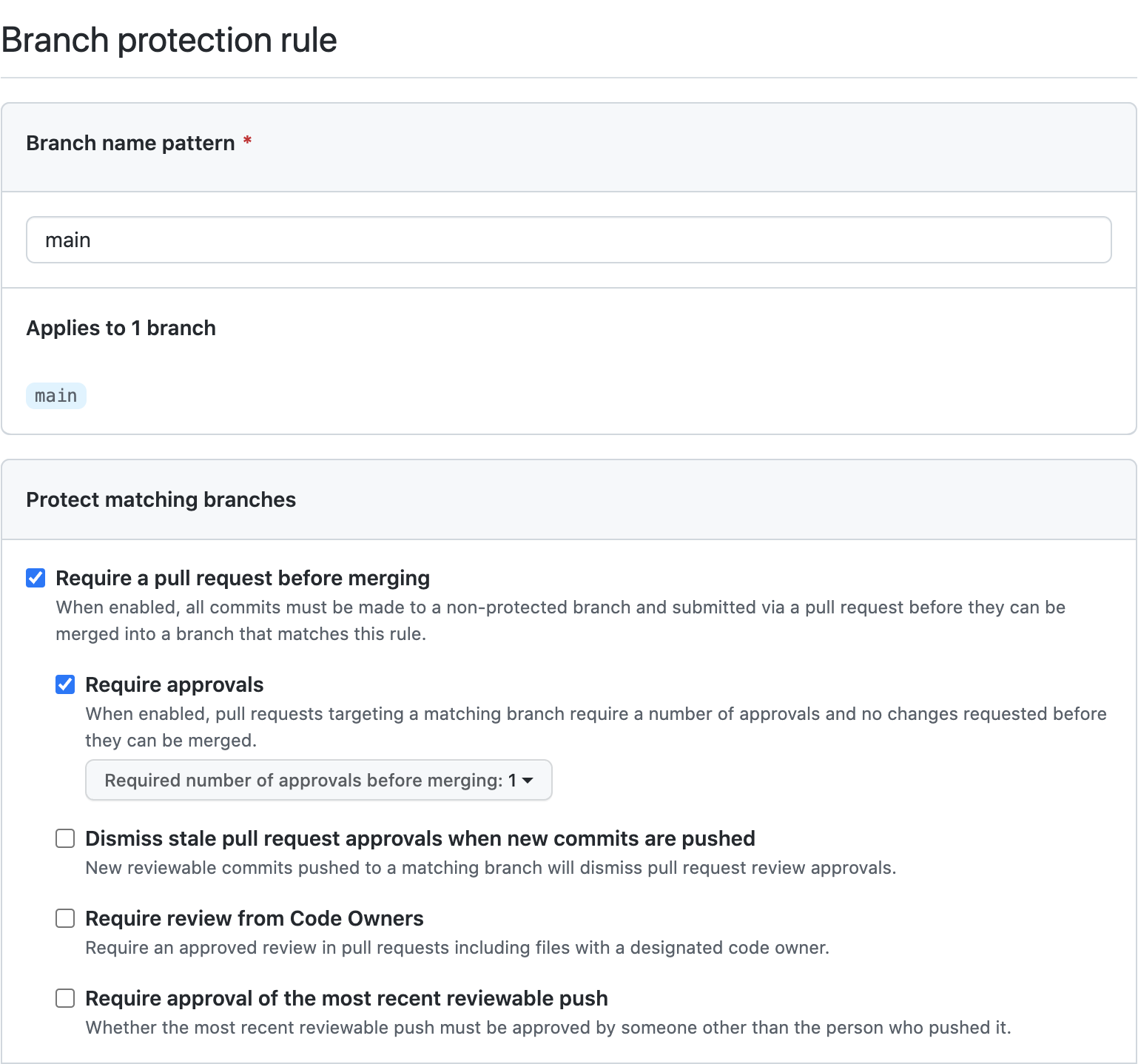
To set these protections, go to Settings > Branches for your respective GitHub repository and click on Add rule. Then check the following criteria:
- Require a pull request before merging
- Require approvals
- Set the required number of approvals, default is
1.
- Set the required number of approvals, default is
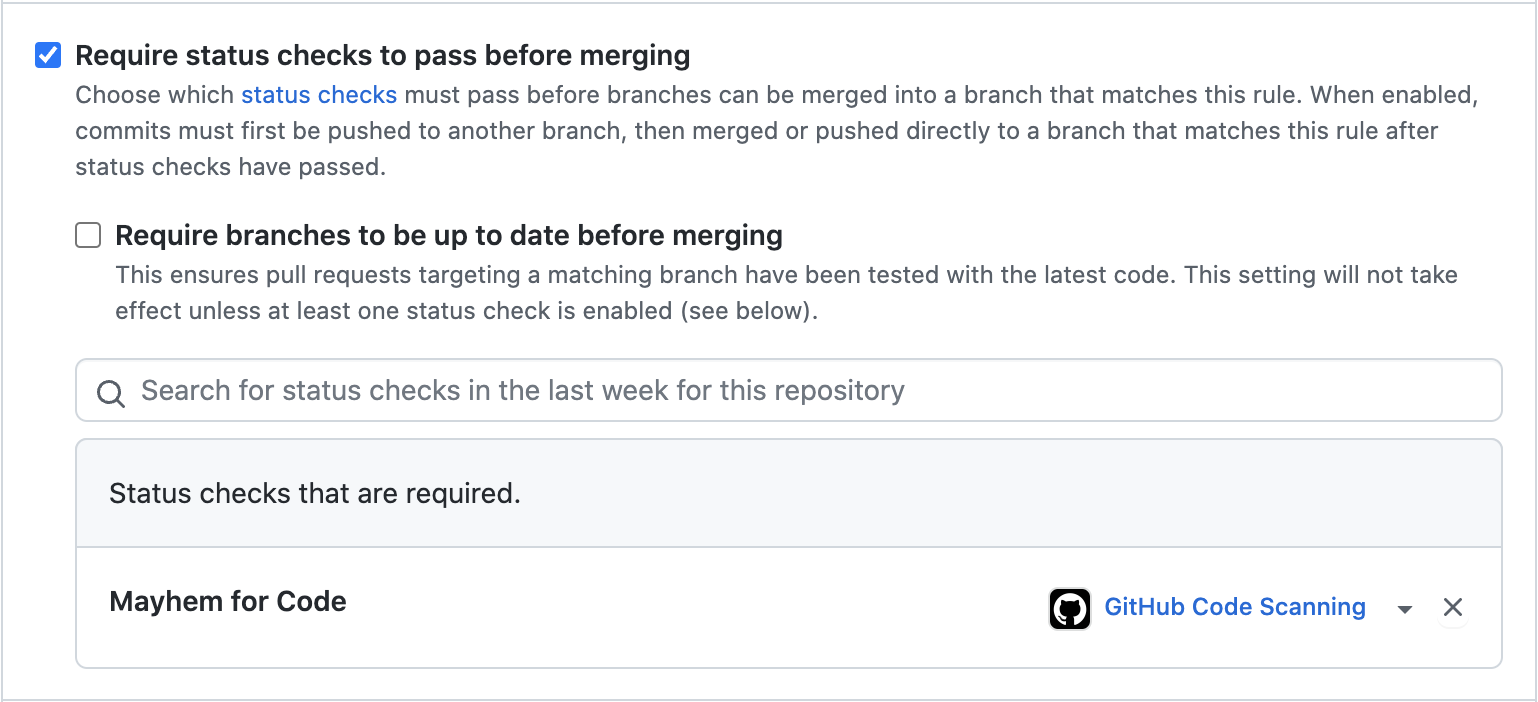
- Require status checks
- Search and set
Mayhemas the required status check.
- Search and set
Note
You may need to run the mCode Action at least once for Mayhem to show up as a required status check.
Once configured, your branch protection settings should look like the following:
Once these protections have been set, we can see how this functions within a pull request where proposed changes are intended to merge into the main branch. The mCode GitHub Action will test target applications for security vulnerabilities and prevent code changes from merging into the primary branch should any vulnerabilities be detected.
Info
The following screenshot shows a pull request whose proposed code changes have been found to have vulnerabilities. Therefore, a developer cannot merge to the main branch (as intended).