Uploading Docker Targets to a Docker Registry¶
With Docker, developers can create Docker images that contain applications and their associated dependencies, and upload or share them so that other developers can avoid having to manage dependencies themselves when attemping to execute the containerized application.
Therefore, when developers run a shared Docker image, the containerized environment is already set up for them—thereby eliminating common dependency-related environment issues associated with packaging and executing shared applications.
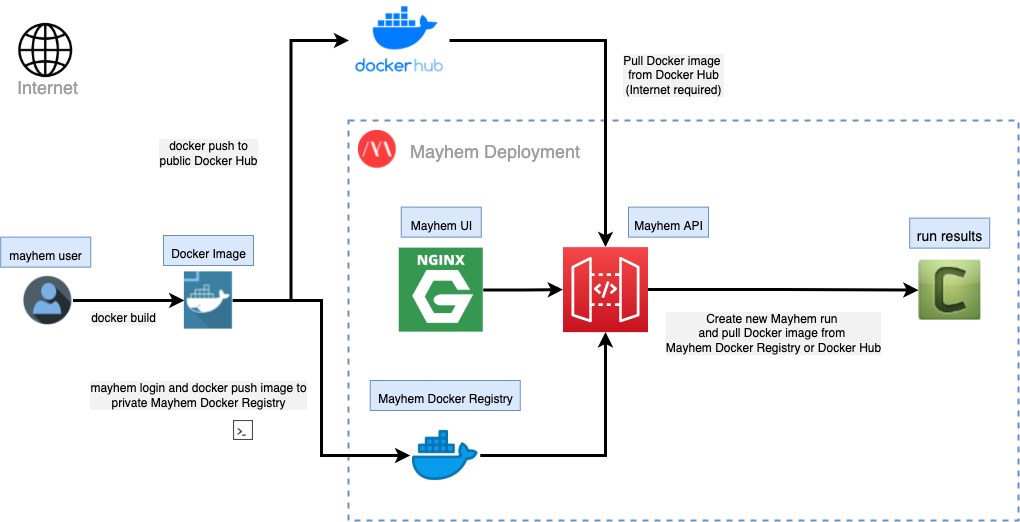
In this regard, Mayhem provides the option for utilizing Docker containers to more reliably manage and execute an application and its dependencies when testing a specified target. However, before Mayhem can utilize Docker containers to test target applications, developers will need to log into and push their image into Mayhem's internal docker registry.
Note
Mayhem also supports non-containerized applications prepared with the mayhem package command. We recommend using this only when containerization is not possible, as it results in slower analysis and triage during testing.
A Docker registry is a storage and distribution system used for easily organizing and sharing tagged or named Docker images.
Mayhem can communicate with an internal docker registry to easily view docker images (such as with the Mayhem UI) and execute runs on target applications contained within these docker images. By default, deployed Mayhem instances already come pre-packaged with an internal docker registry on port 5000.
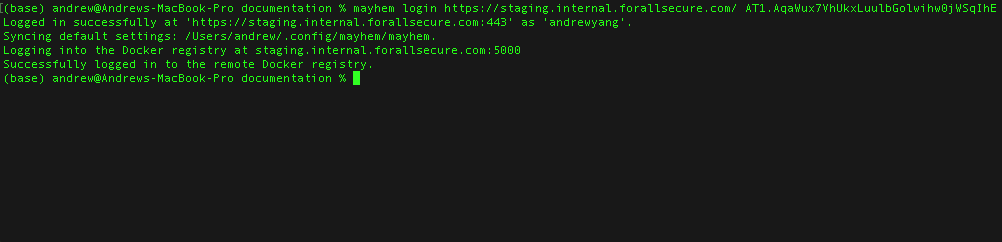
Therefore, the mayhem login command serves two purposes:
- Authenticate with the Mayhem server via the host URL and API Token.
- Login to the internal docker registry located at the host URL (if available).
Tip
Check out Installing the Mayhem CLI and Generating API Tokens for more information on how to use the mayhem login command and generate API tokens, respectively.
Pushing a Docker Image to a Docker Registry¶
Once logged into the internal docker registry, you can now push any new images to the docker registry.
Therefore, for this example, we will create a new image from an existing Docker image and push the new image to our internal docker registry. First, download the 2.10 Tutorial Docker image.
docker pull forallsecure/tutorial:2.10
Next, re-tag the forallsecure/tutorial:2.10 Docker image as docker-upload-tutorial and tag it with the internal Docker registry URL and desired repository name. Finally, push the new image to the internal Docker registry.
docker tag forallsecure/tutorial:2.10 <REGISTRY_HOST>/forallsecure/docker-upload-tutorial
docker push <REGISTRY_HOST>/forallsecure/docker-upload-tutorial
And that's it! You just pushed a new Docker image to your internal Docker registry!
Testing Your Docker Image via the Mayhem CLI¶
As always, you can also use the Mayhem CLI to test an uploaded Docker image existing in the public Docker Hub registry. Simply configure a Mayhemfile and set the image parameter to point to the Docker Hub image along with the containerized cmd target`.
As always, you can also use the Mayhem CLI to fuzz an uploaded Docker image existing in the private Mayhem Docker Registry. Simply configure a Mayhemfile and set the image parameter to point to the Docker Hub image along with the containerized cmd target`.
1 2 3 4 5 | |
1 2 3 4 5 | |
Info
Use the $MAYHEM_DOCKER_REGISTRY variable to specify the URL of the current Mayhem Docker registry. This variable becomes available when users log into the Mayhem Docker registry using the mayhem login command.
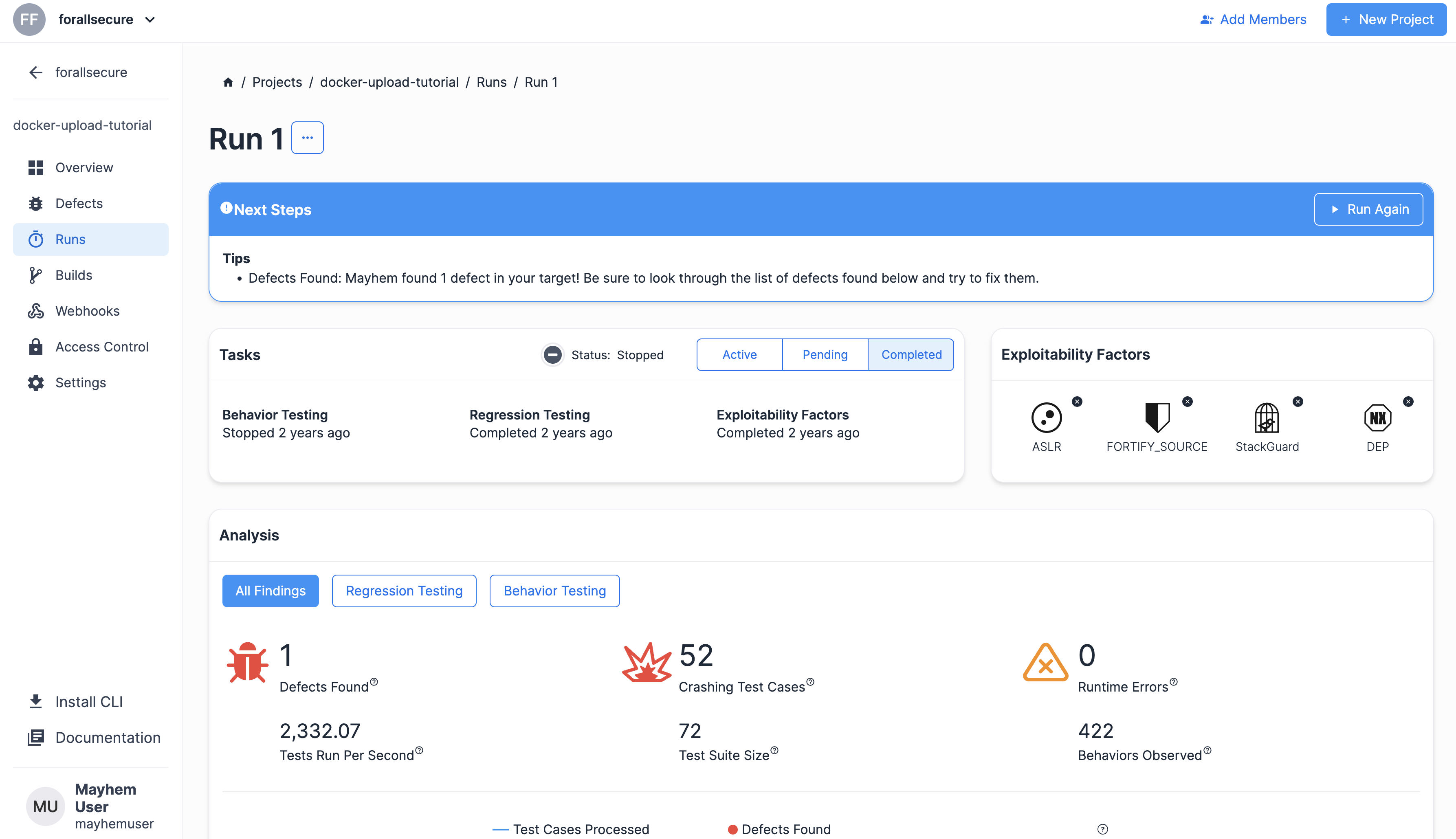
Then, simply execute the mayhem run command for the above Mayhemfile and you should see the containerized application being fuzzed! For example, navigate to the directory of the Mayhemfile and execute the following:
mayhem run .
And that's it! You should now see a Mayhem run for your newly uploaded Docker image.
Docker Registry Permissions¶
By default, all images pushed to the Mayhem registry are accessible to all logged in Mayhem users. However, administrators can configure the registry to enforce access controls that match your organization's project permissions. By turning this on, images in the registry will be associated with projects in Mayhem, and access to those images will be restricted based on the project's permission settings.
This can be configured in the Mayhem Web Console under Admin Settings > User Account Creation and Authorization, by toggling on the Mayhem Registry Access Scoping option.
Summary¶
Using Docker images is a convenient and effective tool for packaging and sharing applications and their dependencies through the use of a containerized environment. Mayhem supports the use of these Docker images and allows users to ingest Docker images from the public Docker Hub registry.
Using Docker images is a convenient and effective tool for packaging and sharing applications and their dependencies through the use of a containerized environment. Mayhem supports the use of these Docker images through the use of its private Docker registry, which has been provided for enhanced user convenience and reliability.
Knowing how to push Docker images to the Docker Hub registry will allow you to fuzz your own uploaded Docker Hub images in Mayhem.
Knowing how to push Docker images into your Docker registry will allow you to utilize the Docker Registry page in the Mayhem UI and easily execute Mayhem runs on target applications within the available docker images.